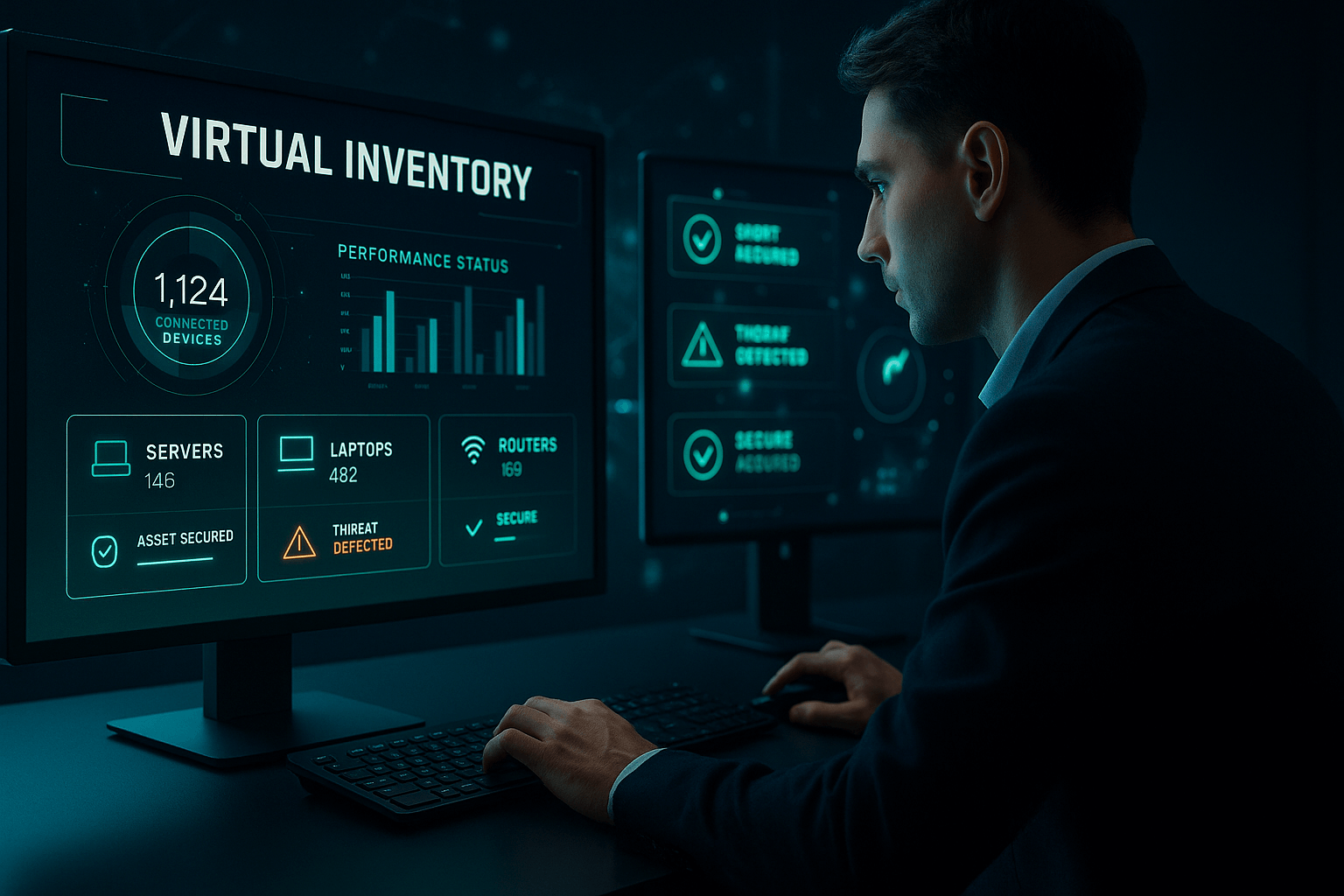
Virtual Inventory Assessments
Discover hidden devices, eliminate risks, and stay audit-ready with a fast, remote inventory scan.
Know What’s Connected. Secure What Matters. Report What Counts.
See what’s really connected across your network, no more blind spots or outdated inventory lists.
Get a full network scan remotely. We won’t slow you down or require any software setup.
Receive clean, compliance-aligned reports that help you prepare for audits and prove what’s secured.
What we offer
See It All. Secure What's Missed.
Instantly detect every device on your network without manual input.
Identify misconfigured assets, unauthorized users, or out-of-date endpoints.
Deliver compliance-friendly inventory snapshots in a click.
Map assets by role, function, or risk for fast policy decisions.
Get expert assessments without hardware or downtime.
Surface unmanaged or rogue devices inside your environment.
Compare inventory snapshots for early threat or sprawl detection.
Ensure asset visibility meets ISO, NIST, and HIPAA readiness goals.
Quickly prove device compliance with on-demand reporting.
Why it matters
No Visibility. More Risk. We Fix That.
Know what’s online, what’s idle, and what’s out of date instantly.
Audit-ready visibility aligned to standards like NIST and ISO.
Arcadia delivers real-time asset clarity and expert-led remediation so your team can act fast and stay compliant.
Run full scans remotely. Zero disruptions. Immediate results.
Delivered by security pros operating from our dual U.S. SOCs.
Frequently Asked Questions
Have Questions About Virtual Inventory Assessments?
Get fast, expert answers to help you decide. Know what to expect, how it works, and why IT leaders trust Arcadia to secure their entire device landscape.
We scan your entire network to identify every connected device, spot outdated systems, and flag unauthorized access. You’ll receive a full report with prioritized recommendations.
Most scans are completed within 48 hours. There’s no need to install software or take your systems offline, everything is done remotely for speed and convenience
No. We break down the findings into clear, actionable insights. You’ll know what devices are at risk, what steps to take, and where to focus first.
Not at all. The assessment is non-intrusive and works silently in the background. Your business stays up and running while we collect the data.
Yes. Our independent inventory validation helps verify what your internal tools may miss, especially for shadow IT, legacy devices, or overlooked endpoints.
You’ll get a custom remediation plan and the option to work with our team to resolve risks, improve compliance, and enhance your network visibility.
Schedule a 1-on-1 with a Cybersecurity Advisor