Cyber Security Services
Real-time protection. Precision defense. Trusted by businesses to stay secure and steps ahead.

Stop Threats. Secure Operations. Stay Ahead.
35% of attacks blocked before inbox delivery
Over 100 targeted attempts intercepted — 25% of all known threats
What we offer
Comprehensive
Cyber Security Solutions
Our Security Operations Centers (SOCs) provide 24/7 real-time threat monitoring, incident response, and log analysis to secure your digital environment.
Safeguard all endpoints: desktops, laptops, mobile devices from malware, ransomware, and unauthorized access.
Protect your business network with advanced firewalls, intrusion prevention systems (IPS), and segmentation to control and secure traffic.
Secure your cloud infrastructure, SaaS platforms, and remote workloads with configuration audits, data encryption, and access controls.
Block phishing, spam, malware, and business email compromise attacks with advanced filtering and threat detection.
Proactively identify, assess, and remediate vulnerabilities across your IT assets before attackers can exploit them.
Leverage actionable threat intelligence to detect emerging risks and respond proactively to global cyber activity.
Simulated attacks by our certified ethical hackers help uncover real-world vulnerabilities in your systems and applications.
Integrate security across endpoints, networks, and cloud platforms to improve visibility, reduce response time, and stop threats faster.
Secure industrial control systems (ICS) and operational technology (OT) from targeted threats that can impact physical processes.
Encrypt sensitive data, prevent data leaks, and ensure fast recovery from breaches or disasters with robust backup systems.
Protect connected devices from unauthorized access, data breaches, and botnet attacks through secure IoT frameworks.
Why Choose Us
Detect Faster. Block Smarter.
Protect Continuously.
Trained specialists who defend against advanced threats in real-time, built on frontline security experience.
We deploy enterprise-grade tools like SIEM, EDR, and advanced firewall systems tailored to your risk profile.
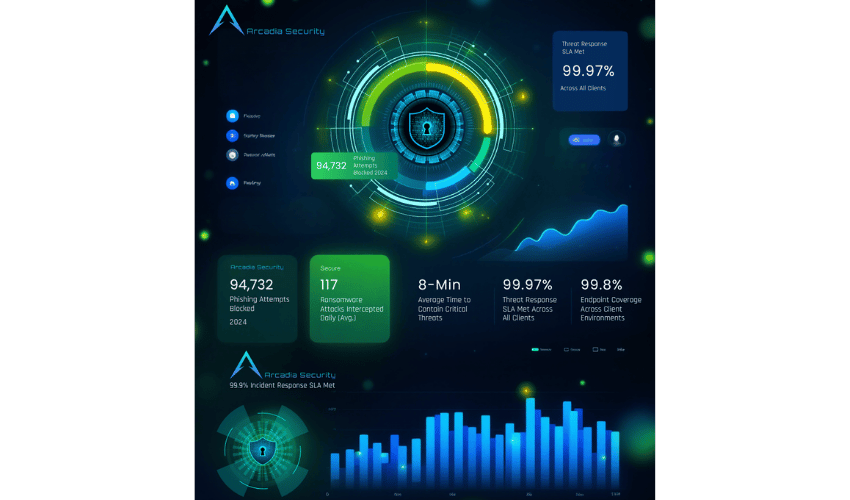
92,000+ Phishing Attempts Blocked (2024),
100+ Ransomware Threats Detected Daily,
99.9% Incident Response SLA Met
Always-on monitoring that intercepts phishing, ransomware, and network intrusions before they cause damage.
Thousands of threats blocked, zero downtime incidents; our prevention-first approach delivers results, not just alerts.
Frequently asked questions
Still Have Questions About Staying Secure?
Get clear, expert answers to help you move forward with confidence. No guesswork — just facts from the frontline of cyber defense.
We detect most threats in real-time, with an average containment time of 8 minutes for critical attacks.
Yes. Our services integrate with most infrastructures — cloud, on-prem, or hybrid — without disrupting operations.
Absolutely. Our threat monitoring and incident response run continuously, with no off-hours.
Not at all. We scale our solutions to fit businesses of all sizes — startup to enterprise — without compromising security.
Simple and guided. We assess your current setup, align on goals, and deploy protection within days — not weeks.
Schedule a 1-on-1 with a Cybersecurity Advisor